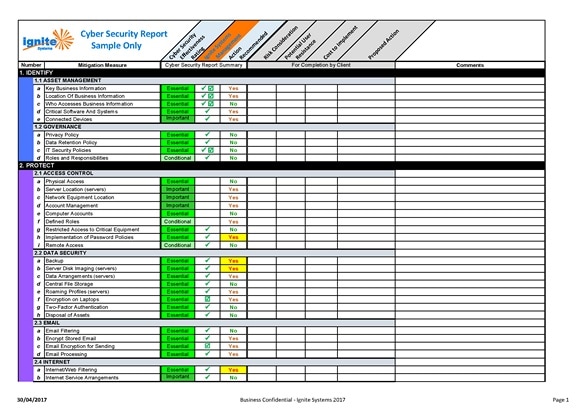
Cyber security assessments
Having effective cyber security starts with understanding your cyber security risks.
Our cyber security assessments will give you an understanding of the cyber risks in your business so you see what the priority risks are and what actions are needed to remediate or eliminate them.
Our cyber security assessments will give you an understanding of the cyber risks in your business so you see what the priority risks are and what actions are needed to remediate or eliminate them.